TunnelBear VPN is a beginner-friendly VPN service known for its simple design, transparent privacy practices, and approachable branding. It helps users protect their online privacy, secure public Wi-Fi connections, and bypass basic geo-restrictions. TunnelBear stands out for its independently audited no-logs policy, easy-to-use apps, and a limited free plan for casual users. It’s best suited for VPN beginners, light browsing, and users who value simplicity over advanced features.
TunnelBear VPN Review is a frequent search among security teams and IT managers evaluating lightweight VPN solutions for staff, contractors, or non-technical users. While TunnelBear is widely known for its friendly branding, this review approaches it from a technical and operational perspective—focusing on cryptography, protocol design, auditability, and real-world performance trade-offs relevant to cybersecurity professionals.
Is TunnelBear VPN safe and private to use in 2025?
TunnelBear VPN implements industry-standard encryption based on AES-256, the same symmetric cipher approved for protecting classified data by multiple government agencies (source: Wikipedia). Key exchange and tunnel establishment rely on modern implementations of OpenVPN and IKEv2, providing forward secrecy and resistance against passive traffic inspection.
From a privacy governance standpoint, TunnelBear distinguishes itself by commissioning annual independent security audits. These audits verify its no-logs claims and infrastructure hardening, a practice still not universally adopted across consumer VPN providers. For organizations assessing vendor risk, this external validation reduces reliance on marketing assertions alone. However, TunnelBear remains a centralized trust model: users must still rely on the provider’s operational integrity, a fundamental limitation of all commercial VPNs.
How fast is TunnelBear VPN in real-world network conditions?
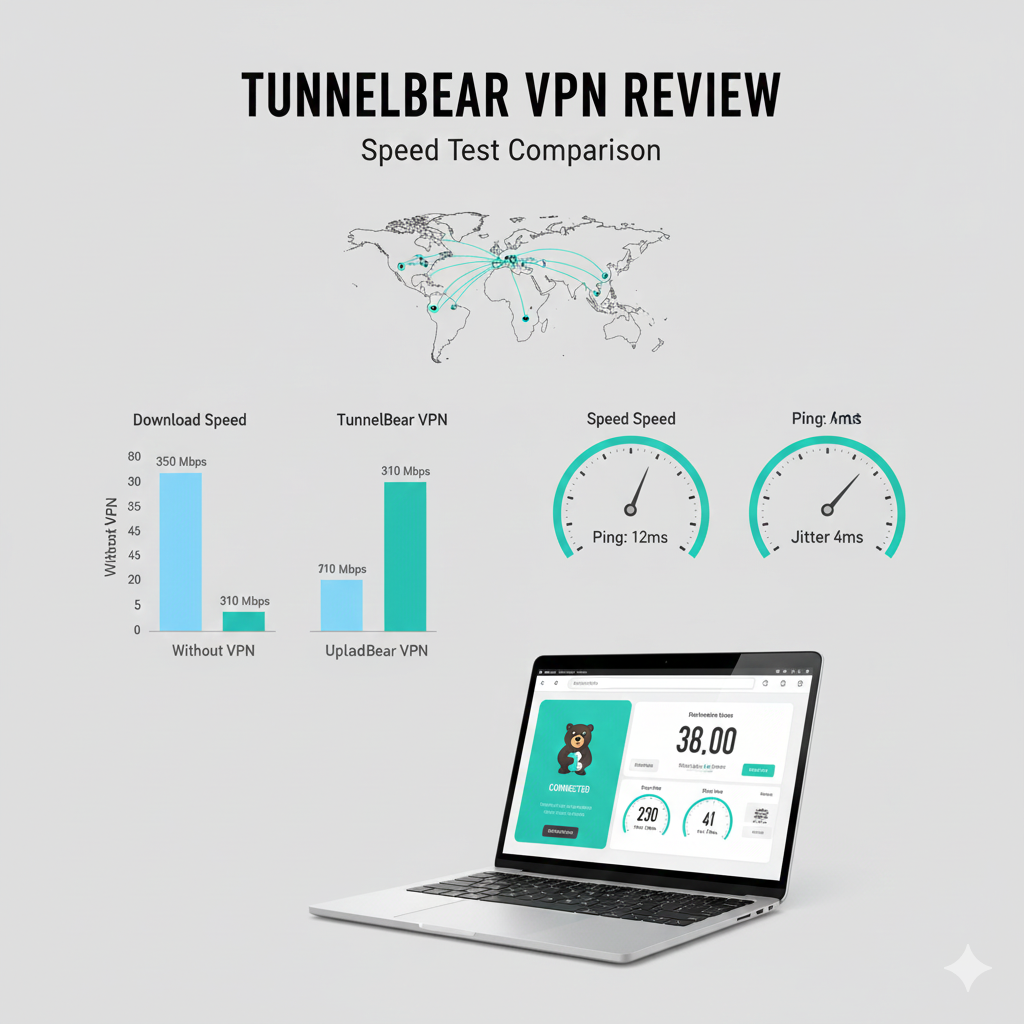
TunnelBear’s performance profile prioritizes stability over raw throughput. On short-hop connections (same country or region), latency overhead is moderate and suitable for encrypted browsing, SaaS access, and routine administrative tasks. Throughput degradation becomes more visible on transcontinental links, where TunnelBear’s smaller server footprint limits routing optimization compared to larger enterprise-focused VPNs.
This behavior aligns with how VPN tunneling introduces encapsulation overhead and additional routing hops, as explained in Cloudflare’s breakdown of VPN packet flow and latency effects (source: Cloudflare Learning Center). For IT teams, TunnelBear’s speeds are acceptable for endpoint privacy but not optimized for high-bandwidth workloads such as large data replication or sustained video delivery.
Constraints and performance:
TunnelBear testing results vary significantly depending on ISP peering, MTU configuration, and device class. Mobile devices using IKEv2 generally reconnect faster when switching networks, while desktop OpenVPN sessions show higher CPU utilization on older hardware. The service does not expose granular transport-level tuning (e.g., TCP vs UDP fine-tuning), limiting performance optimization in constrained or high-loss environments.
Can TunnelBear VPN reliably unblock streaming services?
From a technical perspective, TunnelBear does not market itself as a streaming-optimized VPN, and its infrastructure reflects that positioning. While some users may intermittently access region-locked content, TunnelBear lacks dedicated IP rotation strategies or streaming-specific endpoints. Major platforms increasingly rely on behavioral analysis and ASN-level filtering, areas where smaller VPN networks are more easily identified (source: TechRadar).
For organizations evaluating VPNs for media testing or geo-distributed QA workflows, TunnelBear’s inconsistent unblocking capability represents a functional limitation rather than a defect. Its architecture is tuned for privacy-first use cases, not adversarial evasion of commercial content filters.
How does TunnelBear VPN compare to larger VPN providers?
Compared to large-scale providers with thousands of servers and advanced routing logic, TunnelBear intentionally trades network breadth for simplicity. This design choice reduces operational complexity but also limits redundancy and congestion avoidance during peak usage.
In contrast, providers with more extensive infrastructure investments often deliver higher sustained throughput and better regional failover. A technical comparison with more feature-dense platforms—such as those evaluated in this in-depth analysis of competing VPN architectures—highlights how network scale directly influences performance resilience and protocol flexibility.
At approximately the midpoint of this review, it is useful to contextualize TunnelBear against full-featured alternatives like those examined in the detailed NordVPN performance and architecture review, where advanced protocol options and larger server pools enable broader enterprise applicability.
What are TunnelBear VPN’s main strengths and technical limitations?
TunnelBear’s primary strength lies in its transparency and usability. The client software minimizes misconfiguration risk, which is a non-trivial security benefit in environments with non-specialist users. Its kill switch (“VigilantBear”) operates at the OS network level, reducing the risk of plaintext leaks during tunnel drops.
The limitations are equally clear. TunnelBear does not support WireGuard, lacks configurable split tunneling on some platforms, and provides minimal diagnostic telemetry. For network engineers, this restricts visibility and fine-grained control, making TunnelBear better suited as a personal privacy layer rather than an extensible security control within a broader zero-trust framework.
Is TunnelBear VPN worth the price for professional or organizational use?
From a pricing and licensing perspective, TunnelBear VPN sits in an unusual position. Its paid plans are competitively priced for individual users, yet they lack the centralized management, identity integration, and policy enforcement features typically required by IT departments. There is no native support for SSO, device posture checks, or role-based access controls—capabilities increasingly expected in professional environments.
For cybersecurity professionals, this means TunnelBear should not be evaluated as a replacement for enterprise remote-access VPNs or Zero Trust Network Access (ZTNA) platforms. Instead, it functions best as a privacy-enhancing tool for individuals or small teams with minimal administrative overhead. This distinction mirrors broader differences between consumer VPNs and enterprise-grade tunneling solutions, as outlined in Cloudflare’s discussion of VPN versus Zero Trust models (source: Cloudflare Learning Center).
Who should use TunnelBear VPN—and who should avoid it?
TunnelBear VPN is well-suited for non-technical users, journalists, and consultants who require straightforward encryption on untrusted networks such as hotels or public Wi-Fi. Its minimal configuration surface reduces the likelihood of user error, which is a frequent root cause of VPN misuse and data leakage incidents.
Conversely, network engineers and security architects managing regulated workloads should approach TunnelBear cautiously. The absence of advanced logging controls (even privacy-preserving metadata), lack of self-hosted options, and limited protocol selection restrict its applicability in environments subject to compliance frameworks like ISO 27001 or SOC 2. In these cases, TunnelBear may complement—but not replace—more robust VPN or secure access solutions.
How transparent is TunnelBear’s security model and governance?
Transparency is one of TunnelBear’s most credible differentiators. The company publishes regular transparency reports and submits its infrastructure to independent audits, validating its no-logs posture. This practice aligns with security best practices recommended by industry analysts and reduces asymmetry between provider claims and verifiable controls.
Independent audits are especially relevant given the opaque nature of VPN traffic handling. As the Wikipedia overview of VPN trust models explains, users inherently delegate traffic visibility to the VPN operator, making third-party verification a critical trust signal (source: Wikipedia). TunnelBear’s willingness to undergo recurring audits partially mitigates this structural risk, though it does not eliminate it entirely.
How does TunnelBear handle protocols, tunneling, and cryptography?
TunnelBear relies primarily on OpenVPN and IKEv2, both mature and well-analyzed protocols. OpenVPN offers flexibility and broad compatibility, while IKEv2 provides faster reconnection and better resilience on mobile networks. However, the absence of WireGuard is notable, particularly as WireGuard gains adoption due to its smaller attack surface and improved performance characteristics.
From a cryptographic standpoint, TunnelBear’s implementation follows accepted standards without attempting proprietary enhancements. This conservative approach reduces the risk of introducing novel vulnerabilities but also limits performance optimization. For readers seeking a deeper understanding of how VPN protocols encapsulate and protect traffic, the formal definition of tunneling mechanisms in IETF documentation provides valuable context (source: RFC Editor).
How does TunnelBear VPN fit into modern security architectures?
In modern security design, VPNs increasingly coexist with endpoint detection, identity-aware proxies, and encrypted DNS rather than operating as standalone controls. TunnelBear fits this model as an endpoint-level privacy layer rather than a central enforcement mechanism.
Its lack of deep integration options means it is unsuitable for scenarios requiring traffic segmentation, site-to-site connectivity, or application-aware routing. These use cases are better addressed by dedicated concentrators or site-to-site VPN deployments, which are discussed in more detail in this technical overview of VPN concentrator architecture and multi-tunnel design.
Does TunnelBear VPN introduce measurable operational risk?
Any VPN introduces operational trade-offs, including increased latency, potential MTU mismatches, and reliance on third-party infrastructure. TunnelBear mitigates some risk through stable client software and conservative defaults, but it offers limited observability when issues arise. There are no exposed logs, metrics, or diagnostics suitable for root-cause analysis beyond basic connection status.
For security teams, this lack of visibility can complicate incident response. If anomalous behavior is detected at the application layer, correlating it with VPN activity is difficult without telemetry. As a result, TunnelBear should be deployed with a clear understanding of its role and limitations within the broader security stack.
How does TunnelBear VPN perform under regulatory and compliance scrutiny?
For organizations operating under regulatory constraints, the use of consumer VPNs requires careful risk assessment. TunnelBear VPN does not position itself as a compliance-ready solution, and it does not provide contractual assurances, data residency controls, or compliance mappings to standards such as GDPR, HIPAA, or PCI DSS. This is not a flaw per se, but a scope limitation.
That said, TunnelBear’s audited no-logs policy reduces exposure related to data retention and unauthorized disclosure. According to guidance from Kaspersky on VPN privacy models, no-logs claims only carry operational weight when independently verified (source: Kaspersky Blog). TunnelBear’s audit history therefore improves its standing relative to unaudited competitors, though it remains insufficient for environments requiring formal compliance attestations.
Can TunnelBear VPN be safely used alongside other security controls?
TunnelBear VPN is generally compatible with endpoint firewalls, EDR platforms, and DNS-layer protections. Because it does not attempt deep packet inspection or application-level filtering, it rarely interferes with host-based security tooling. This makes it suitable as a supplementary control rather than a core enforcement mechanism.
However, TunnelBear does not natively support split tunneling in all environments, which can complicate coexistence with internal network monitoring tools. Traffic routing decisions are largely opaque, limiting administrators’ ability to exclude specific subnets or services. For comparison, more configurable providers—such as those evaluated in this detailed ExpressVPN security and performance review—offer finer-grained traffic controls that better align with layered security architectures.
What are the long-term scalability and vendor risk considerations?
Vendor risk extends beyond encryption strength and into ownership, financial stability, and operational continuity. TunnelBear is owned by a larger cybersecurity company, which provides a degree of long-term stability and resource backing. This reduces the likelihood of abrupt service discontinuation, a non-trivial risk in the VPN market.
Scalability, however, remains limited by design. TunnelBear does not provide APIs, centralized management consoles, or deployment automation hooks. As a result, scaling usage beyond a handful of endpoints introduces administrative friction. For IT managers, this means TunnelBear is best treated as a tactical tool rather than a strategic platform.
How does TunnelBear VPN compare to alternative privacy technologies?
It is important to contextualize TunnelBear VPN alongside adjacent privacy technologies such as encrypted DNS, secure proxies, and browser isolation. VPNs provide full-tunnel protection but at the cost of performance overhead and trust delegation. Alternatives may offer narrower protection scopes with less operational impact.
Cloudflare’s educational material on encrypted DNS explains how DNS-layer security can mitigate certain threats without full traffic tunneling (source: Cloudflare Learning Center). TunnelBear VPN complements these technologies but does not replace them. Security architects should view it as one component in a defense-in-depth strategy rather than a standalone safeguard.
What decision framework should professionals use when evaluating TunnelBear VPN?
For IT managers and cybersecurity professionals, the evaluation of TunnelBear VPN should begin with a clear definition of use case. If the goal is to provide simple, reliable encryption for individual users on untrusted networks, TunnelBear performs competently and with a commendable level of transparency.
If the objective includes centralized policy enforcement, compliance reporting, or network segmentation, TunnelBear will fall short. In such scenarios, a combination of enterprise VPNs, secure access service edge (SASE), or ZTNA solutions is more appropriate. Understanding these distinctions prevents misalignment between tool capabilities and security objectives.
Is TunnelBear VPN worth recommending in 2025?
TunnelBear VPN occupies a narrow but defensible niche. It prioritizes usability, transparency, and baseline security over configurability and scale. For professionals advising non-technical users or evaluating low-friction privacy tools, it represents a lower-risk option compared to opaque, unaudited providers.
At the same time, it should not be misconstrued as a comprehensive security solution. Its limitations in protocol diversity, management visibility, and enterprise integration are material and must be acknowledged in any serious risk assessment.
Conclusion
In conclusion, TunnelBear VPN Review from a professional standpoint reveals a service optimized for simplicity and trust rather than performance maximization or enterprise control. It is a credible choice for individual privacy protection and light professional use, but it does not replace enterprise-grade VPN or zero-trust solutions. When deployed with clear expectations and within appropriate boundaries, TunnelBear VPN can serve as a useful, if limited, component of a modern security toolkit.